Our Solution
SecureKloud understands that technology and the competitive landscape are subject to frequent change. To stay ahead in this landscape, SecureKloud has developed a unique and proven strategy to constantly innovate, mature, and expand on the core technical components of any solution.
We at SecureKloud call this strategy as Cloud DevOps for Innovation and Maturation (CDIM). This strategy enables our DevOps and DevSecOps team to not only work on the Customer's day-to-day Cloud operations but adopt the current best practices, tailoring them to fit the Customer's strategic vision and evolving from a DevOps to a NoOps-capable Operational Model.
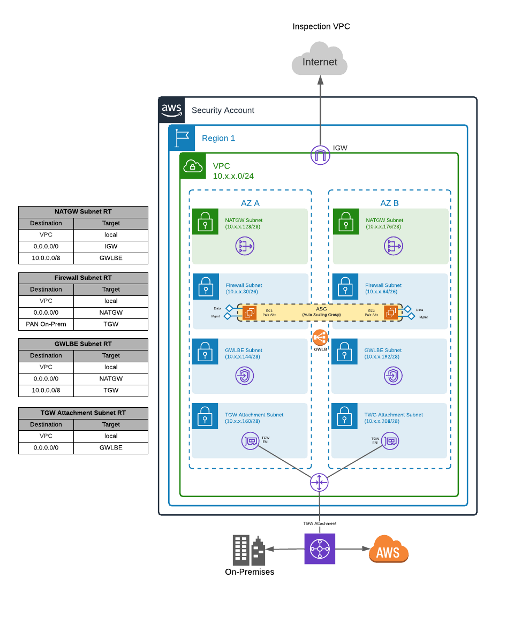
As SecureKloud is already engaged with this organization as their AWS Managed Services Partner and follows the CDIM approach, SecureKloud was given the opportunity to design and develop Security Inspection VPC to remediate the customer issues. The Inspection VPC is based on Palo Alto Firewalls and all the surrounding VPC deployment is done to provide resiliency and scalability of the solution.
Palo Alto Firewall running in High Availability mode inspects all Inter/Intra region traffic within the AWS region instead of traversing all over to on-premises.
The Inspection VPC deployment utilizes the Gateway Load Balancer (GWLB), which simplifies the deployment, scalability, and management of third-party virtual appliances in a VPC. It provides one gateway for distributing traffic across multiple virtual appliances while scaling them up or down based on demand. This eliminates potential points of failure in the network and increases availability.
The main downside of this deployment method, compared to traditional FW clusters, is that it is not able to synchronize sessions between elements. So, in the event of a firewall failure, sessions must be re-established in order to permit the traffic through another firewall in the Auto Scale Group (ASG).
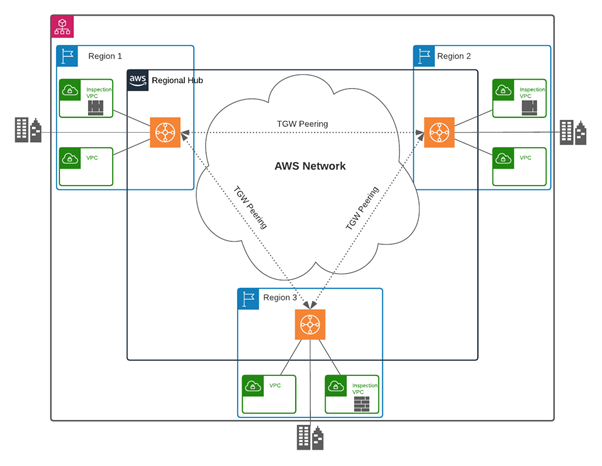
The Transit Gateway (TGW) performs centralized routing between all VPCs, the on-premises network, and other AWS regions. There is one TGW per region and all VPCs are attached to it. All TGWs are interconnected in a full mesh via TGW peering. This allows for direct connectivity between any two regions without needing to traverse the on-premises network.
Traffic between regions is always routed through the Security Inspection VPC in both the source and destination regions. This is done to simplify the TGW routing and operational support of the platform. Since all east-west traffic is required to be inspected by the Security Inspection VPC, no VPC peerings are created between VPCs.
Continuous monitoring of AWS direct connect links are in place to keep a check on the link utilization using CloudWatch Metric alarms in line with AWS best practices, if the link gets utilized beyond 90%, an SNS notification has been configured to send an email to our 24x7 Managed Security Services team.
Transit Gateway Flow Logs are configured to capture IP traffic flow to and from TGW and logs are being published to Amazon CloudWatch. This provides our managed security services team with end-to-end network visibility with more granular flow-level metrics in Transit Gateway.