- 8Minutes
- 1454Words
- 9Views
The new advancements in technology like the IoT, Blockchain and many others have expanded the horizons of the IT industry, especially in the cloud space.
As we are heading towards a post-pandemic era, companies and entrepreneurs have become more tech-savvy and they are trying to adopt innovative technologies that make their work easier. And of course, cloud adoption has a major role to play.
Lots of companies have adopted Cloud Computing but the real question is- Are we secure?
Definitely not, and cloud security threats will continue to escalate if you overlook it.
In this blog, we’ll discuss the top cloud security threats and cloud vulnerabilities that you should protect your business from in 2023 and beyond. With the ever-growing amount of critical business data and applications in the cloud, it is critical to ensure that your information assets are not vulnerable to these cloud security concerns.
Save Your Business from These 10 Cloud Security Threats
1. Misconfigurations of cloud security settings
According to a recent study, misconfigurations were found to be the cause of 95% of cloud security vulnerabilities. It can be caused due to simple reasons and can happen at various levels. Misconfigurations can occur at the infrastructure level with security groups or with Network Access Control List (NACL).
Chances are also high that it might occur at the application level. For instance, misconfiguration occurs when an application is deployed at the Kubernetes level and a key is exposed in the etcd file. It could also happen if an IAM user has a lot of privileges. So, there might be a lot of keys that could be exposed, raising serious cloud security risks.
Because many enterprises with multi-cloud deployments are not so familiar with protecting their cloud infrastructure using the right tactics, a misconfiguration or safety negligence can easily expose the cloud-based resources to attackers.
2. Lack of organic security (DevSecOps) as part of application development
You don’t want to have security as an afterthought. As the application development passes through different phases, organic security is in-built along with the application when it is bootstrapped. Without DevSecOps, you might not spot any vulnerabilities or untested codes during the application development process. And you might need to grapple with these concerns at the very end. So, with DevSecOps, security is assured at different levels of application development.
At every stage of deployment, you need to use the right tools to have the DevSecOps done perfectly. Security is in-built right from the design stage, coding stage, development, publishing, production, etc. At every single point! It could be application security. It could be the testing of an application from a security standpoint. It could be secure certificates. It could be the handling of the keys. In short, security is assured right from the initial stages as opposed to worrying about it at the end of the deployment process.
3. Authorization as a result of non-zero security permissions
One of the most important aspects of cloud to look into is the non-zero security permissions. In this situation, you trust the user and give all the permissions to the user as you are confident that he/she will use them only in the best interest of the company. But what if that user’s account gets hacked? Obviously, you wouldn’t be prepared for this particular data breach. The hacker will get access to important critical systems and all data, including ones with confidential information.
4. Lack of cloud-native security tools
Security threats can arise due to the lack of cloud-native security tools. In recent years, cloud has moved from standard web application development to container-based deployment.
By 2023, about 80% of the enterprises will have at least two container-based production applications in any cloud. Right now, it stands at 15% and it will take a phenomenal jump in the next three years.
So, you need cloud-native security tools to monitor those microservices and APIs to make sure they are secure, and no unauthorized user can access confidential data. Deployment of the clusters should be another key area to be monitored, especially with the proxies accessing them.
5. Multiple identities from other enterprises accessing data
There are a lot of risks associated with multiple identities, which can be formed in an enterprise in different ways. For instance, it can be your own users or users from another enterprise through a federation or a Single Sign-On (SSO) process. It could also be your own users accessing from an active directory or a shared directory location.
This issue should be brought under control as they can gain easy access to enterprise data and applications in systems. So, users have to be controlled in such a way that somebody cannot piggyback into their identity and cause havoc in the system. You should pay attention to this security factor irrespective of your cloud environment whether you operate on a private cloud or a public cloud.
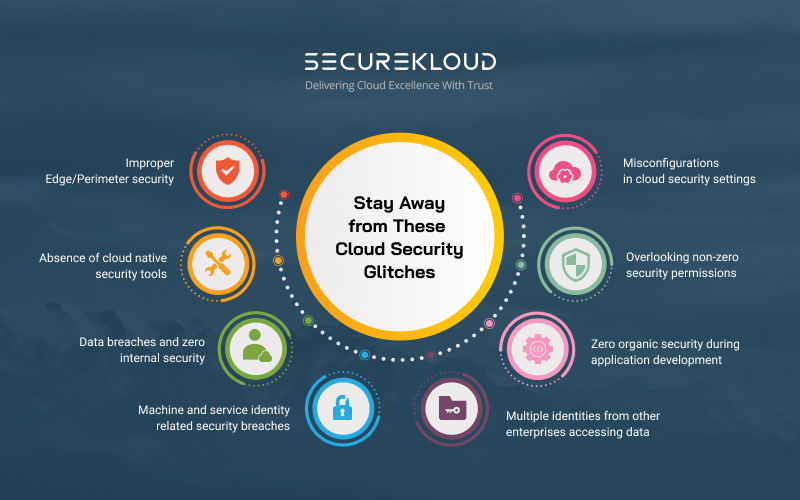

6. Rising internal security threats and data breaches
Threats come not just from external sources but from internal as well. Hence, it’s critical to secure your systems from internal threats. It can be unintentional in some cases as people might leave the backdoor open and some processes might be running without any security certificates. Another user can plug in and gain backdoor entry into the systems. One of the real-life data breaches caused by internal threats is the Marriott Hotels & Resorts data leak due to a compromised third-party app, affecting almost 339 million guests and the company had to pay a fine amount of £18.4M.
On the other hand, there could also be real conscious attempts internally where an insider can exploit your system to damage or steal data. But whether it is intentional or accidental, these insider threats can lead to a data breach, system downtime, and data loss, all indirectly leading to reduced customer confidence.
7. Machine and service identity related security breaches
These security breaches happen when anyone can get to the service part that is exposed, whether it’s a service layer or the machine layer. These are the most important parts for any enterprise. You wouldn’t want these layers to be hacked, especially at a time when most of the enterprise architecture is moving towards the services part.
8. Improper Edge/Perimeter security
Edge security might look new to you, but it has really picked up a lot in the last couple of years, especially in 2021. There are various reasons why Edge/Perimeter security has gained momentum. The primary factor is the advent of new technologies like IoT and Blockchain. When you have edges that need to be a part of the networks, decentralization is the best way to optimize Edge and Perimeter security.
Edge security ensures the security of the corporate resources that are not located within a centralized datacenter. Thus, it will secure the users and apps that function at the edge of your company’s network.
9. Lack of device tracking and improper access control
Closely connected to Edge security is the security of the devices that are going to be plugged into these Edge locations, such as your IoT device, laptop, desktop, mobile device, and so on. Even the mobile device can cause problems if it is not properly controlled, especially when it comes to its access control.
10. Lack of cloud security strategy and cloud computing skills
Cloud computing can open up vulnerabilities for enterprises that lack cloud security knowledge and the skills to effectively combat cloud security challenges. Traditional data center security models are not effective for the cloud and hence your IT team should be aware of developing and implementing a proper security architecture framework, cloud security strategy, the ins and outs of the shared responsibility model, etc. Without an effective strategy and skillsets in place, your business can be vulnerable to cloud security issues, resulting in reputational damage, financial losses, and compliance issues.
These are some of the major threats that you need to be watchful of in the coming years. As you have now read through the major cloud security threats, now is the time to learn about how to rise above these threats. Explore what our thought leaders had to share about the Cloud Security and Compliance trends that you need to follow in 2023 and beyond.
You can check out the entire webinar video here.
Why SecureKloud?
The certified Cloud professionals at SecureKloud ensure Cloud security and compliance to help you thrive in your business without any security breaches. Our 10+ years of expertise in cloud has given way to 400+ satisfied customers in our Cloud portfolio. With our diligent team of cloud experts, we have been consistently providing end-to-end Cloud Managed Services for various companies, including the F500 ones. Need help solving any of these cloud security issues? Contact us.