Executive Summary
This case study describes the challenges our customer faced around compliance and cloud security to protect their data protection on cloud, and the solution provided by SecureKloud.
About the Client
Reigning among the world’s largest 100 suppliers to the automotive industry, our client is the market leader in parking heaters, roofs, and convertible roof systems. Furthermore, they concentrate on the growth market electromobility with heating systems, charging solutions, and battery systems.
Business Challenges Faced by the Client
Compliance and data protection in the cloud have been a major challenge for client due to shared responsibility model and automation of public cloud infrastructure. Hence, to ensure consistent compliance controls across their infrastructure, they required new methodologies.
Here are some of the key areas where our client required continuous compliance:
- Confirmation whether all AWS users have passwords matching the organization’s password policy
- Log all the user actions in the AWS account
- Ensure that IAM-related activities are tracked and alerted using Lambda
- Identification of all the unattached AWS resources such as Volumes
- Ensure all the instances are launched inside a VPC and SSH traffic is allowed only from the known IP addresses
- Enable Multi Factor Authentication (MFA) for the users
- Confirm all the EC2-related activities are tracked and notified using Lambda and CloudWatch
SecureKloud Solution/Approach
As a part of ongoing engagement with the client for Cloud Monitoring and DevOps support, SecureKloud implemented the usage of AWS Config and now continuously monitoring it to help them achieve continuous compliance across their infrastructure.
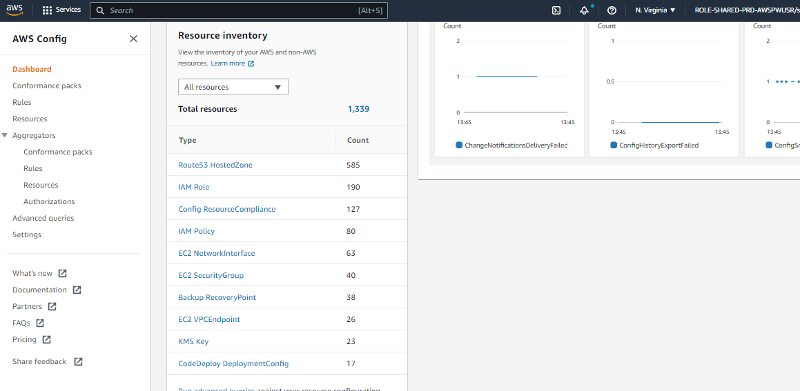
AWS Config provides a detailed view of the resources associated with the AWS account, including how they are configured and how they are related to one another. Continuous Compliance is being achieved by the client through SecureKloud Services.
AWS Lambda is used to write custom Config Rules. SecureKloud is monitoring and configuring whenever required, the following AWS Config Rules to ensure the client’s continuous compliance needs are met in the environment.
- Untagged EC2 resources – Checks whether the resources have at least one tag attached to it
- IAM password policy enabled – Checks whether the account password policy for IAM users meets the specified requirements
- Cloud Trail enabled – Checks whether AWS CloudTrail is enabled in the AWS account
- Unattached Volumes – Checks whether EBS volumes are attached to EC2 instances
- MFA for IAM Users – Checks whether the IAM users in the AWS account require multi-factor authentication for console sign-in
- EC2 instances within a VPC – Checks whether the EC2 instances belong to a virtual private cloud (VPC)
- Disallow unrestricted incoming SSH traffic – Checks whether security groups that are in use disallow unrestricted incoming SSH traffic
- Instances launched with approved Instance types – Checks whether all the EC2 instances in the AWS account are of the approved instance types
- IAM User Policy Check – Checks that none of the IAM users have policies attached
- AWS Config Rule – Checks whether the tags and passwords are in place
Business Benefits
- Continuous Monitoring:
With AWS Config, our client could continuously monitor and record configuration changes of their AWS resources over a given period.
- Continuous Compliance:
AWS Config allowed client to achieve continuous auditing and assessment of overall compliance of their AWS resource configurations with the organizational policies and guidelines.
About SecureKloud
Client
World Market Leader in Automotive Industry
Sector
Automotive
Technology
AWS