Our Solution/Approach
As a part of ongoing engagement with the client for Cloud Monitoring and DevOps support, SecureKloud implemented the usage of AWS Config and now continuously monitoring it to help them achieve continuous compliance across their infrastructure.
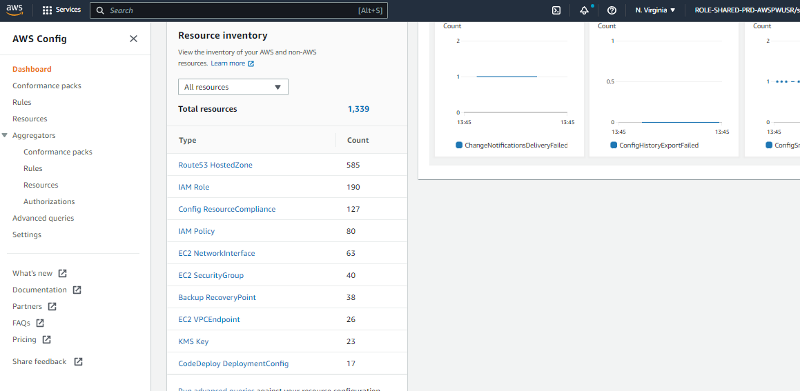
AWS Config provides a detailed view of the resources associated with the AWS account, including how they are configured and how they are related to one another. Continuous Compliance is being achieved by the client through SecureKloud Services.
AWS Lambda is used to write custom Config Rules. SecureKloud is monitoring and configuring whenever required, the following AWS Config Rules to ensure the client's continuous compliance needs are met in the environment.
- Untagged EC2 resources: Checks whether the resources have at least one tag attached to it
- IAM password policy enabled: Checks whether the account password policy for IAM users meets the specified requirements
- Cloud Trail enabled: Checks whether AWS CloudTrail is enabled in the AWS account
- Unattached Volumes: Checks whether EBS volumes are attached to EC2 instances
- MFA for IAM Users: Checks whether the IAM users in the AWS account require multi-factor authentication for console sign-in
- EC2 instances within a VPC: Checks whether the EC2 instances belong to a virtual private cloud (VPC)
- Disallow unrestricted incoming SSH traffic: Checks whether security groups that are in use disallow unrestricted incoming SSH traffic
- Instances launched with approved Instance types: Checks whether all the EC2 instances in the AWS account are of the approved instance types
- IAM User Policy Check: Checks that none of the IAM users have policies attached
- AWS Config Rule: Checks whether the tags and passwords are in place